
Malwares are the public enemy of the modern digital era. Approximately there were almost 5 billion malware attacks in the year 2021. Let’s know about what malware is, different types of malware and how to keep your personal computer or organization safe from malware attacks in this article.
What is Malware
Malware is a shortened form of malicious software. It denotes any harmful computer program that is created to do harm to a computer system. They are unwanted software intentionally designed to unsettle the normal behavior of a computer, server, client, network etc and steal or leak sensitive information, data or even access in various forms. .
Different Types of Malware
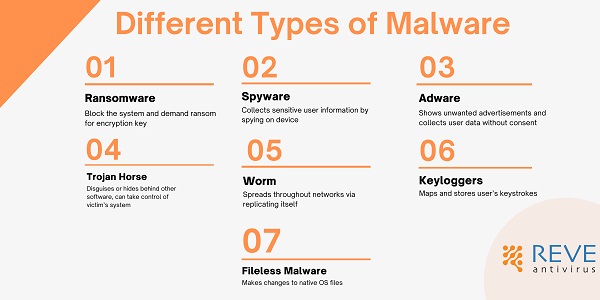
Types of malware
These harmful programs come in different forms with different targets and approaches. Let’s look at some very common malware
| Malware Name | Malware Function |
| Ransomware | Block the system and demand ransom for encryption key |
| Spyware | Collects sensitive user information by spying on device |
| Adware | Shows unwanted advertisements and collects user data without consent |
| Trojan Horse | Disguises or hides behind other software, can take control of victim’s system |
| Worm | Spreads throughout networks via replicating itself |
| Keyloggers | Maps and stores user’s keystrokes |
| Fileless Malware | Makes changes to native OS files |
Ransomware:

In today’s world, ransomware is probably the most threatening and dangerous malware. Once it gets entry to a system it encrypts files, folders or even the whole OS and demands ransom in an untraceable mode of payment for the decryption key.
Worldwide ransomware attacks are on the up, in 2021 alone almost 500 million ransomware attacks were estimated. It is also predicted that, by 2021 the expense for ransomware victims will reach 6 trillion dollars annually!
Spyware:
Spyware is another dangerous type of malware. It can work on the background and steal sensitive information like passwords, pins, payment information etc. What’s more frightening is, spyware is not only functional in desktop or browser, it can also affect smartphones as well.
Adware:
Who willingly wants to see an advertisement? None right? Well, an adware just forces you to do so! It displays pop-up ads that often have no relevance or acceptance to you. Not only is it annoying but also it takes up resources and slows the machine down. Furthermore, adware’s activities are often not limited to displaying forced ads. Collecting personal data, redirecting to other advertising sites, even changing internet browser settings, default browser and search settings as well as homepages can also be done by more advanced malicious adwares.
Trojan Horse:
As the name suggests, when a trojan horse, or simply “Trojan” is disguised in such a way that it looks like a normal, harmless file or program. This file is designed to trick a user into downloading and installing malware inadvertently into their system.
However, as soon as a Trojan is installed, cyber criminals get a free pass to the system and are ready to exploit it. It is possible to steal data, install more malware, modify files, monitor user activity, destroy data, steal financial information, conduct denial of service (DoS) attacks on targeted web addresses, and more using the Trojan horse malware. In a worse case scenario, if it is combined with a worm, the damage can be extreme.
Worm:
Just like a worm in nature, a computer malware named as worm can replicate itself over and over. It targets vulnerabilities in operating systems to install themselves into networks. They can also be spread via phishing attacks. Once a worm has got access to a machine, it not only can infect the machine, but in some cases it can affect the whole network as well. They are capable of infecting large numbers of computers and consume bandwidth overloading the web servers in the way.
Keyloggers:
Keyloggers can be referred to as a special type of spyware which can record the keys struck in a keyboard without the knowledge of the user. This assists the hacker to steal passwords, banking information or other sensitive information.
Fileless Malware:
These are different types of malware which are very well disguised and do not install or change anything initially. However, they are capable of making changes directly to the files like PowerShell that are native to the OS. What makes it so dangerous is, as these files are considered as a legitimate file, fileless attacks are often not caught by a cybersecurity software!
How Does Malware Get Entry?

A malware can get entry in various ways. However, most common sources of malware spread include email attachments, malicious websites, torrents, and shared networks. Here are some examples
Phishing: Phishing links containing emails are probably the most common way of malware entry. These mails come from frauds and try to snatch sensitive user data. Nowadays, not only email but also sms or in instant messaging apps are also used for the purpose as well.
Torrents: Though file sharing via torrent is already banned in many countries in the world but for some less technologically advanced countries, people are still using different torrent clients. These files are always suspected and considered as a way of malwares to get entry to a new machine.
Flash drives: Connecting a public flash drive which is used in public networks without scanning it for malwares contains a high chance for malware spread.
How to Stay Safe From Malwares
Malwares can wreak havoc to any personal or organizational network. Enough cybersecurity awareness is a must for the safeguard. To win the fight against malwares, support of a modern and advanced cybersecurity product is necessary. An antivirus software which can detect any kind of malware threats and take prompt action to restrict any kind of loss.
- RaaS : The Dark Side of SaaS
- Hackers Target MOVEit Transfer’s Zero-Day Vulnerability, Emergency Patch Deployed
- How Scammers Are Utilizing ChatGPT? Few Tips To Be Safe
- World Backup Day: Why Data Backups are Important in Cybersecurity
- What is Social Engineering and How Cyber Criminals Use It
- Things To Know About Personally Identifiable Information (PII)
- What is Data Breach? Why and How It occurs? How To Prevent Data Breach


